Introduction
Security isn’t just a checkbox anymore. It’s a moving target, especially in the mobile world.
Mobile apps today carry more than just features. They carry data, identity, access, and trust. And if that trust is broken? You don’t just lose users.
You lose credibility.
You lose sleep.
And sometimes, you lose everything.
This is where Zero-Trust Mobile Security steps in, not as a patch, but as a mindset. One that says: trust no one, verify everything. No matter how close they seem to your app’s ecosystem.
Whether it’s a banking platform or the best untraceable text app, users expect their data to remain private and secure. Every app threat, from malware to API abuse, demands a proactive response.
Why now?
Let’s look at the numbers.
The Global Zero Trust Security Market was priced at USD 36.35 billion in 2024. It is estimated to increase to 124.50 billion by 2032, with a CAGR of 16.7%.
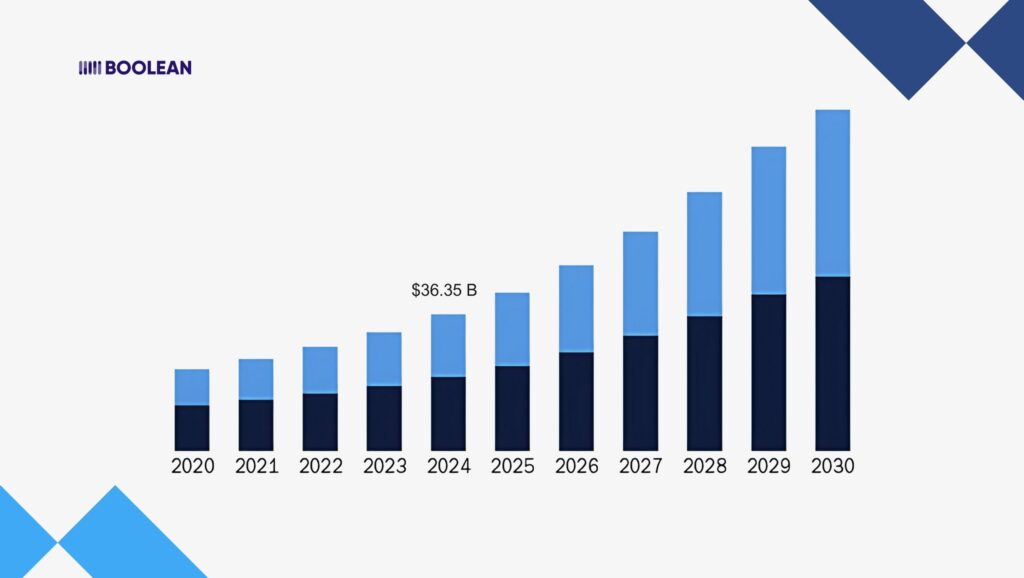
That’s not a small bump. That’s a seismic shift.
And North America alone made up 35.57% of that market in 2024. Adoption is accelerating, and fast.
But here’s the disconnect:
While zero-trust is gaining traction in enterprise IT, mobile app development still lags behind. Many apps are still being built with trust assumptions baked in:
- Trusting the device.
- Trusting the network.
- Trusting static credentials.
- Trusting that the user hasn’t been compromised.
Sound familiar?
Yeah, it’s risky.
Zero-trust flips that script. It questions every access request. It monitors every interaction. And it assumes that threats can come from inside just as easily as from outside.
This guide is here to help you make sense of all that.

You’ll learn what zero-trust mobile really is (and what it’s not). You’ll see where it fits into modern app development.
And most importantly, you’ll discover how to integrate it in a way that’s smart, secure, and sustainable.
No fluff. Just practical, thoughtful guidance.
So if you’re tired of crossing your fingers every time your app hits production, stick around. There’s a better way to build. And it starts here.
What is Zero-Trust Mobile Security?

Let’s clear one thing up right away:
Zero-trust mobile security isn’t just a feature. It’s a security philosophy. It’s based on a core principle:
“Never trust. Always verify.”
In the zero-trust environment, no device, user, or app component relies automatically on being inside your network or already certified. Every access request is considered potentially hostile until otherwise proven.
Sounds paranoid? Maybe.
But in today’s threat landscape, it’s smart.
The zero-trust began as a broad concept-something is known as zero trust architecture. This was designed to protect the enterprise systems against data violations, insider threats, and lateral movement in the network.
But now, with the explosion of mobile apps and cloud-native services, securing cloud applications has become just as critical as protecting on-device data.
In a mobile context, zero-trust isn’t just about securing a backend.
It’s about protecting the entire app experience:
- User identity
- App logic
- Data transmission
- API endpoints
- Runtime behavior
All of it. End-to-end.
And if you’re aiming to be a top mobile app development company, then secure development practices need to be baked in, not bolted on.
Where Traditional App Security Falls Short
Here’s the problem: Many users still rely on outdated security frameworks that assume the app or user is “safe” once authenticated.
Once that initial handshake happens, the gates are wide open.
This makes mobile apps highly vulnerable to:
- Credential stuffing
- API abuse
- Token replay
- Reverse engineering
- Jailbroken or rooted environments
What Makes Zero-Trust “Mobile”?
Great question.
Zero-trust mobile is adapted for the specific challenges and constraints of mobile platforms. That means:
- Lightweight, client-side app hardening
- Secure-by-default permission models
- API-level segmentation
- Runtime app security for detecting tampering or anomalies
- Tight integration with mobile identity management systems
In other words, it is not only implementing a desktop-based (or server-based) zero-trust concept on mobile.
It is about creating a mobile-first trust border that follows the user, device, and data flow wherever they can be.
Why This Matters for Developers (and Businesses)
If you’re managing a complex software development technology stack, this shift to zero-trust is not optional. It’s foundational.
You can’t scale a mobile app securely without it.
You can’t deliver true mobile app scalability if your backend is wide open.
That’s why companies are embracing zero-trust apps as a competitive edge, not just a security checkbox.
Why Zero-Trust Matters in App Development
Unlike tightly controlled enterprise environments, your app ends up on thousands, even millions, of devices. Different operating systems. Different permission settings. Different user behaviors.
And unfortunately… different attack surfaces.
That’s why traditional, perimeter-based security models just don’t cut it anymore. They assume that once someone gets past the “gate,” they’re good to go.
But mobile doesn’t have gates. It has shifting lines. Blurred edges.
It needs a zero-trust mobile. Whether it’s a corporate tool or an anonymous application, every mobile app needs robust security.
A New Kind of Risk Demands a New Kind of Defense
Every mobile app is a potential target.
From the moment it’s installed, it becomes exposed to:
- Malware
- Fake apps
- Tampering
- Rooted or jailbroken devices
- Reverse engineering
If your app still trusts the device just because it’s “yours”?
That’s a problem.
Zero-trust principles for mobile shift the mindset. They assume compromise. They enforce constant suspicion. It might sound cold. But it’s safe. And smart.
From One-Time Checks to Ongoing Vigilance
What happens after the user logs in?
In many apps, not much. But in a zero-trust mobile environment, the story doesn’t end there; it starts there.
You monitor continuously.
You apply dynamic permission checks.
You perform continuous security verification in real-time.
Because access decisions shouldn’t be frozen in time. They should evolve based on behavior, context, and device posture.
That’s how you stay ahead of the game. That’s how you defend your users while giving them a smooth experience.
Securing the App, At Its Core
A core component of every secure mobile experience is runtime app security.
This means your app can identify whether it is being altered while it’s running.
It can respond to:
- Rooting or jailbreaking
- Debugging attempts
- Code injection
- Cloned or modified versions of your app
Think of it like an immune system.
If something shady happens? The app reacts. It locks down. It protects the data.
This is the new standard for mobile app endpoint security.
And it’s critical for maintaining a healthy trust boundary on every single device. This is especially critical for intellectual property mobile applications where code and data represent significant business value.
Core Principles of Zero-Trust for Mobile Apps
You’ve probably heard the phrase by now: “Never trust. Always verify.” This is the zero-trust.
But when you are making a mobile app, what does it really mean?
How do you change that philosophy into real, actionable design?
Let’s break it.
Zero-trust is not just a discussion for mobile apps. It’s a set of practical security principles built on top of a zero trust architecture and tailored to meet the challenges of real-world mobile environments.
These principles help you rethink mobile security from the inside out.
- Continuous Verification
In traditional app security, once a user logs in, they’re in.
That’s it. That’s the check.
But with zero-trust mobile, verification never stops.
You’re continuously evaluating:
- Device trustworthiness
- User behavior
- App integrity
- Network risk level
This is continuous security verification in action. Services like cash advance app instant approval use risk-based authentication to maintain security without slowing user experience.
- Least Privilege Access
Your app shouldn’t hand out broad permissions “just in case.” Instead, it should only grant the minimum access needed, just in time, and only if it’s truly necessary.
This is where dynamic permission checks shine. They evaluate risk on the fly and make access decisions based on:
- Location
- Device health
- Role or usage pattern
No more over-permissioned users.
No more exposed surfaces.
Just smart, contextual app development security.
Whether it’s a banking app or a text message hiding app, permissions should be granted only when absolutely necessary.
- Enforce Strong Identity
Identity is everything in zero-trust apps.
If you can’t verify who is accessing your app, you can’t protect what they’re accessing.
That’s why mobile identity management and zero trust authentication are foundational.
And it’s not just about the user. You need to verify:
- The device
- The app instance
- The network
Together, they form your trust boundary mobile, the invisible fence that guards your entire mobile ecosystem. Zero-trust assumes every interaction could be an app threat until proven otherwise.
- Harden the App
If you’re not using mobile app hardening, your app is vulnerable.
Attackers are continually attempting to reverse-engineer or tamper with mobile applications. They exploit unsecured code, exposed secrets, and weak encryption.
With app hardening, you:
- Obfuscate critical logic
- Block tampering at runtime
- Prevent debugging or code injection
This is runtime app security in motion, and it’s non-negotiable in a secure mobile development lifecycle.
Combine it with mobile encryption (for data at rest and in transit), and you’ve got a tough shell and a strong core.
- Secure APIs
Most mobile apps rely on APIs. That’s where the real data lives. That’s where the real risk lives, too.
Without app API security, attackers can:
- Intercept requests
- Replay tokens
- Manipulate responses
Zero-trust demands that every API call is verified, not just once, but constantly. Also cash advance apps particularly benefit from zero-trust API security to prevent fraud and protect user financial data
Apply zero-trust best practices like:
- Token rotation
- Request throttling
- Behavioral analytics
- Micro-segmentation
Your backend should only talk to what it fully trusts, and nothing more. This extends beyond mobile to cloud applications security, ensuring your entire ecosystem is protected.
Want enhanced functionality without compromising security? These free APIs for mobile apps are zero-trust friendly.
- Build with Zero-Trust in Mind
If you wait to bolt on zero-trust later, you’ll always be playing catch-up. Instead, design a secure mobile architecture from the ground up.
Use a zero-trust SDK if available.
Follow modern security frameworks and secure development guidelines.
Build trust boundaries into every layer: front end, API, authentication, and runtime.
This isn’t just about risk mitigation.
It’s about building mobile app zero trust into the DNA of your product.
Think Beyond Today – Make Security Scalable
What protects your app today might not protect it tomorrow. That’s why zero trust mobile apps are designed to evolve.
Whether you are managing the mobile app security, scaling globally, or integrating new services in zero-trust, apps that keep your safety model tight and future-proof.
Even if you are working in custom software development, the principles are the same.
Create an app that scales without expanding the surface of the attack.
Keep it all together.
Here’s the truth: users did not thank them for saving them. But they will punish you if you don’t.
By embracing zero trust principles for mobile, you’re not just guarding data; you’re earning trust, one interaction at a time.
This is the foundation of secure mobile development. This is how top mobile app development companies stay ahead of the curve.
How to Integrate Zero-Trust into Mobile App Development
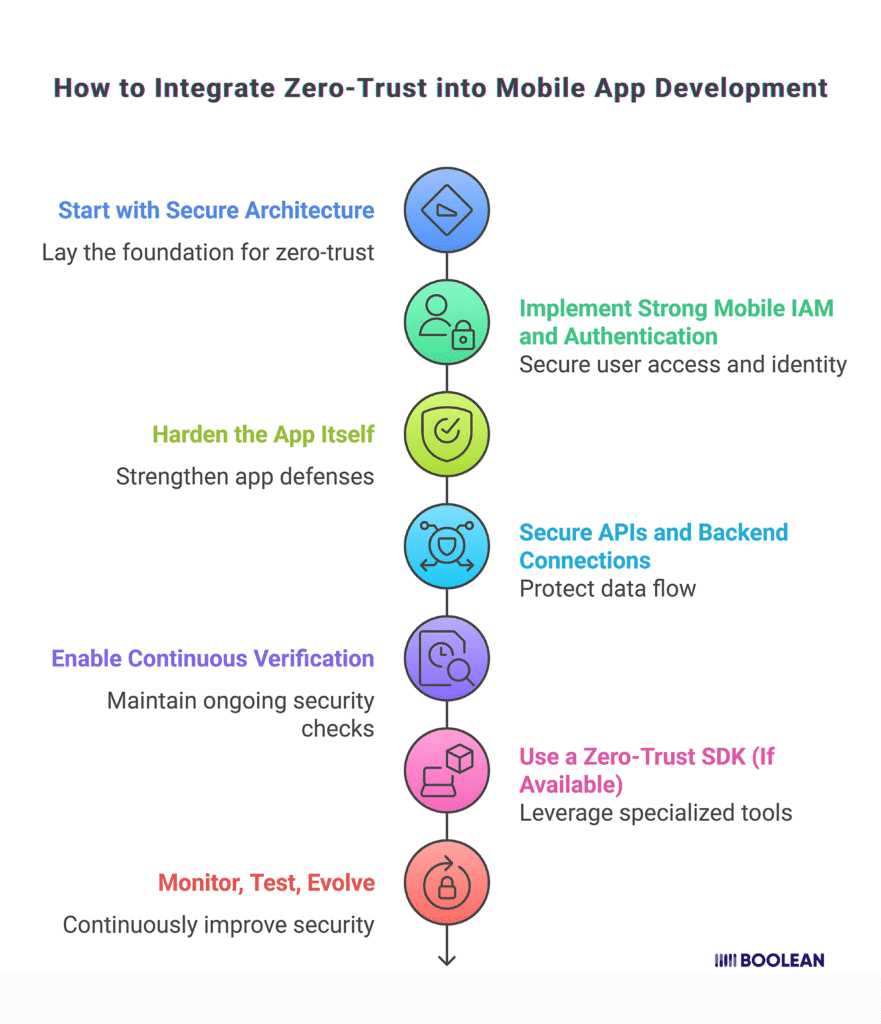
Let’s get practical. You understand why zero-trust matters. Now let’s talk about how to make it real, without overwhelming your team or user experience.
The creation of Zero-Trust Mobile Apps is about aligning with a perfect security structure, being active with design, and layering in control that adapts as your app scales.
Here is your step-by-step game plan:
Step 1: Start With Secure Architecture
Everything begins with the right secure mobile architecture.
Design your system assuming compromise. That means segmenting access, enforcing policies, and never trusting by default.
Use principles from zero trust architecture to:
- Identify your attack surfaces
- Define trust boundaries
- Map data flows between app components
- Separate authentication from authorization
This sets the foundation for every other security layer that follows.
Step 2: Implement Strong Mobile IAM and Authentication
Strong identity is non-negotiable. Use IAM to enforce contextual user identity, not just a username and password. Even when users ask ‘can you send a text anonymously?’, proper identity verification prevents abuse.
Deploy zero trust authentication by verifying:
- Device posture (rooted, secure, outdated?)
- User behavior patterns
- Geo or network risk
- Session anomalies
Add biometric auth where appropriate. And don’t rely on just tokens, rotate them regularly, and make sure they expire quickly. Even an anonymous application needs proper identity management to prevent abuse while maintaining user privacy.
Step 3: Harden the App Itself
Before your app talks to an API or verifies identity, it has to protect itself.
Apply comprehensive mobile app hardening:
- Code obfuscation
- Anti-tamper mechanisms
- Certificate pinning
- Emulation & root/jailbreak detection
- In-app runtime checks (runtime app security)
This reduces the risk of reverse engineering and ensures mobile app endpoint security is taken seriously. For intellectual property mobile applications, code obfuscation and anti-tampering mechanisms are non-negotiable.
Step 4: Secure APIs and Backend Connections
Your app isn’t just about what runs on the device. Most of the real power happens server-side.
Use app API security strategies like:
- Role-based access control
- API key rotation
- Token scoping
- Rate limiting
- JSON validation & sanitization
- Per-session encryption
This approach is essential for securing cloud applications that your mobile app connects to, ensuring end-to-end protection.
Follow zero-trust best practices: verify every API request. Even internal traffic. Even from “trusted” apps. Every. Single. Time.
Step 5: Enable Continuous Verification
Once the user is authenticated and active, your job isn’t over.
Set up continuous security verification:
- Monitor sessions for unusual activity
- Auto-expire sessions on risk signals
- Validate permissions with dynamic permission checks
- Require re-auth for high-risk actions
This aligns with zero trust principles mobile: trust should always be earned, moment to moment.
Step 6: Use a Zero-Trust SDK (If Available)
You don’t have to build everything from scratch. Many security platforms now offer zero-trust SDKs built specifically for mobile. These include modules for:
- Identity verification
- Secure sessions
- Behavior analytics
- Threat detection
- In-app responses (blocking, alerting, or hiding sensitive data)
A good SDK gives you secure development without reinventing the wheel. It speeds up implementation while maintaining high app security standards.
Step 7: Monitor, Test, Evolve
Security isn’t one-and-done. Use mobile-specific app threat protection tools to monitor:
- Real-time attacks
- App clone attempts
- Network-based threats
- Compromised user sessions
Set up alerts. Automate responses. And keep your team in the loop.
Remember: zero-trust in apps is a living system. It should evolve as your codebase, user base, and risk surface grow.
Step 8: Bake It Into Your Development Process
Zero-trust doesn’t belong at the end of the roadmap; it belongs in your app development security lifecycle.
Integrate secure coding into CI/CD.
Run security tests early and often.
Educate your team about trust boundary mobile design.
And make app hardening part of every release.
This is secure mobile development in action.
You do not need to do all this at once. But every step you move towards zero-trust reduces the risk, increases flexibility, and the user earns trust.
By applying these layers – architecture, authentication, app hardening, runtime protection, and smart API design – you make something rare:
A mobile app that’s both functional and fearless.
Best Practices for Secure Mobile App Development
Building secure mobile apps isn’t just about reacting to threats; it’s about designing with protection from the start. Here’s how to do it right:
- Use Mobile App Hardening Tools
Tools that obfuscate code, prevent tampering, and detect rooted or jailbroken environments add a vital layer of mobile app hardening.
They help protect your app even when running in risky environments. Whether addressing ‘can you send a text anonymously?’ or securing financial transactions, zero-trust principles remain consistent.
- Perform Static and Dynamic Analysis
Scan your code before and during runtime.
Stable analysis finds quick weaknesses in development, while dynamic analysis helps capture real-world issues during execution-important to maintain security apps.
- Adopt DevSecOps Practices
Shift to the left. Integrate security in your CI/CD pipeline. With devsecops, safety checks, coding, and testing, your team’s DNA forms a safe growth part of DNA.
- Follow Zero-Trust Best Practices for Mobile
Assume nothing. Verify everything.
Implement zero trust authentication, continuous security verification, and dynamic permission checks to ensure access is earned, not assumed. Modern mobile apps must consider cloud applications security as part of their overall zero-trust strategy.
These best practices aren’t just suggestions. They’re how you protect your users, your data, and your brand.
Tools & Frameworks for Zero-Trust Mobile Security
You do not need to start from scratch when creating a zero-trust mobile app. Equipment is a complete ecosystem of libraries and safety structures designed to help you do better, not harder.
Below is a curated mixture of war-tested solutions, mobile safety, and app plays a unique role in ensuring hardening and runtime protection.
Let’s look at them together.
- Appdome – No-Code Mobile App Security

Appdome offers a no-code platform for integrating zero-trust SDKs, anti-tampering, mobile encryption, and secure communications, all without touching your source code.
It’s ideal for:
- Mobile app hardening
- Runtime app security
- Preventing reverse engineering and fraud
It’s like putting your app in a smart, reactive armor; customizable and constantly evolving.
Read Also: Low Code Mobile Development Platforms: The Future of App Development
- OWASP Mobile Security Testing Guide (MSTG)

The OWASP MSTG is a go-to SOS manual for safety. It provides a wide structure for both stable and dynamic testing, which helps you assess weaknesses throughout the mobile stack.
Perfect for:
- Following zero-trust best practices
- Implementing secure mobile architecture
- Creating a security-first QA process
Tip: Combine MSTG with the Mobile App Security Checklist for development checklists.
- Auth0 – Identity and Access Management (IAM)

Auth0 makes it easy to integrate secure, scalable mobile IAM and zero trust authentication with:
- Multi-factor authentication (MFA)
- Risk-based authentication
- Social and passwordless login
Auth0 handles it perfectly, whether you’re building for enterprise or consumer apps. Users often wonder ‘is t-mobile secure as good as digital secure?’ – the answer depends on the zero-trust implementation.
- Zimperium – Mobile Threat Defense

Zimperium provides real-time mobile app threat protection, capable of detecting and responding to:
- Jailbreak/root detection
- SSL inspection
- Malware, spyware, and more
Their SDK can be embedded directly into your app to deliver continuous security verification, in line with zero trust principles for mobile.
- Google SafetyNet / Play Integrity API

For Android apps, SafetyNet (and its successor, Play Integrity) helps you validate the device’s health.
You’ll be able to:
- Confirm the app isn’t tampered with.
- Check for rooted or compromised devices.
- Protect your backend using app API security.
Together, they enhance your app development security posture on Android. Many users ask, ‘what is digital secure app on Android?’ These are security solutions that implement zero-trust principles at the device level.
- Microsoft Entra (formerly Azure AD) – Enterprise-Grade Zero Trust IAM

Microsoft Entra supports zero trust architecture through unified identity and access management, especially for enterprise mobile apps.
Great for:
- Mobile identity management
- Securing internal enterprise apps
- Integrating with broader secure development pipelines
- CI/CD & DevSecOps Integrations – GitHub Actions + Snyk
Want to bring zero-trust to your workflows? Use GitHub Actions for automation and Snyk to scan for early open source weaknesses in the Dev cycle.
Ideal for:
- Adopting DevSecOps
- Protecting your software development technology stack
- Automating your secure mobile development pipeline
These tools don’t replace strategy; they enable it. Use them to build a secure mobile architecture layer by layer. Many ask ‘is Verizon Digital Secure safe?’ – like all security tools, its effectiveness depends on proper zero-trust implementation.
Protect your users. Defend your APIs. Strengthen your mobile app endpoint security.
Real-World Use Cases of Zero-Trust Mobile Security
This is a strategy being used by companies around the world, now the right to protect mobile experiences from the dangers that have developed.
Even consumer apps like the best untraceable text app rely on zero-trust principles to protect user anonymity and prevent data leaks. Privacy-focused apps that teach users how to send an anonymous text from an iPhone must implement zero-trust to protect user identities.
Let’s examine some real-world examples where the zero-trust mobile safety concept has transformed into behavior, with apps improving safety, reducing violations, and creating smart, secure digital ecosystems.
- Banking Apps Preventing Fraud with Continuous Verification
A leading European digital bank implemented zero trust architecture in its mobile app after suffering repeated credential stuffing attacks. Financial services, from traditional banking to modern cash advance apps, require the highest security standards.
What changed?
- They introduced continuous security verification to monitor user behavior in real time.
- Used dynamic permission checks to restrict high-risk transactions until identity was re-verified.
- Hardened the app with runtime app security and mobile app endpoint security.
The result: A 70% drop in fraud attempts and significantly faster detection of unauthorized sessions. Even cash advance app instant approval services implement zero-trust to balance speed with security.
- Healthcare App Enforcing Secure Access Across Devices
A global health platform, dealing with highly sensitive patient data, adopted zero-trust best practices across its mobile application.
Key strategies:
- Integrated zero trust authentication using biometric + device posture checks.
- Applied mobile IAM for role-based access, ensuring nurses and doctors could only see data relevant to them.
- Implemented mobile encryption and trust boundary mobile policies to separate public and private access points.
Impact: They passed stringent HIPAA audits and prevented multiple unauthorized access attempts through compromised devices.
- E-Commerce App Securing APIs and Payment Workflows
A top e-commerce company in North America transitioned to zero-trust mobile after detecting API scraping and bot abuse on its Android app.
Their solution:
- Adopted a zero-trust SDK to secure API calls dynamically.
- Used app API security features to identify and block unusual traffic patterns.
- Hardened the frontend with mobile app hardening to prevent reverse engineering.
Outcome: API abuse was reduced by 90%, while checkout performance remained smooth and uninterrupted for users.
- Travel App Scaling Globally Without Sacrificing Security
When a fast-growing travel booking app expanded into new regions, it needed a secure mobile development approach that scaled.
Here’s how they used zero-trust in apps:
- Integrated zero trust principles into their CI/CD pipeline with automated risk checks.
- Used tools like Appdome and Microsoft Entra to implement secure development and IAM across borders.
- Deployed mobile app threat protection to catch region-specific malware strains targeting travelers.
The result: Seamless expansion into 10+ markets with no major security incident.
- Enterprise BYOD (Bring Your Own Device) Strategy
A Fortune 500 company shifted to a mobile-first workforce, but with that came risk.
- They rolled out a zero-trust mobile app strategy to protect internal tools used by employees on personal devices:
- Devices were required to meet baseline security checks (via trust boundary mobile controls).
- Access was gated using zero trust authentication and mobile identity management.
- Sensitive data was real-time time contained, encrypted, and tracked.
Impact: Reduced data leakage, improved employee productivity, and fully aligned with company-wide zero trust architecture.
It does not matter that your industry is banking, healthcare, retail, or enterprise; zero-trust mobile safety is no longer optional.
It is flexible, today’s most reliable apps. It’s how they defend users, APIs, and data in a world where threats never sleep.
Build like them. Protect like them.
Common Challenges & How to Overcome Them
Here are the most common challenges users face and how to solve them.
Challenge 1: Legacy Systems and Architecture
- Problem: Older apps weren’t built with zero trust architecture in mind.
- Solution: Start with incremental improvements, like adding zero trust authentication or separating trust boundaries in your API layers.
Challenge 2: User Friction
- Problem: More security often means more steps for users.
- Solution: Use mobile IAM, biometrics, and risk-based auth to keep it seamless. Authenticate silently when possible. Only challenge users when something feels “off.”
Challenge 3: Keeping Up With Threats
- Problem: Mobile threats evolve fast, too fast.
- Solution: Use mobile app threat protection tools with continuous security verification. Stay proactive with alerts, patches, and runtime monitoring.
Challenge 4: Tool Overload
- Problem: Too many tools, not enough integration.
- Solution: Choose platforms that offer unified SDKs or all-in-one secure development features. Focus on tools that align with your existing security frameworks and tech stack.
Zero-trust principles apply universally, from enterprise tools to consumer apps like a text message hiding app.
Zero-trust takes effort, but it’s not out of reach. Start small. Keep users in mind. And build with security at every stage.
Choosing a Mobile App Development Company with Zero Trust Expertise
If you’re serious about building zero-trust mobile apps, choosing the right development partner is critical.
Not all vendors are built the same. You need a team that understands zero trust architecture, mobile security, secure mobile development, and mobile app hardening, not just a beautiful UI.
Look for these qualities:
- Proven experience with zero-trust SDKs and mobile IAM
- Strong portfolio in app API security and runtime app security
- Ability to implement continuous security verification and dynamic permission checks
Boolean Inc., a recognized top mobile app development company, stands out in this space.
They blend secure design, smart development, and real-world zero-trust best practices to create scalable, resilient mobile apps.
Whether it’s enterprise, healthcare, or fintech, Boolean Inc. builds with trust at the core.
Conclusion
Mobile security isn’t just a checkbox anymore. With users expecting safety by default and attackers growing smarter every day, relying on traditional defenses just isn’t enough.
Integrating zero-trust mobile security is not to complicate your development process, but to guide secure development from the inside out.
By following zero trust architecture, using mobile IAM, and implementing app hardening and mobile encryption, you’re not just protecting your app; you’re protecting people. Their data. Their trust. Whether users are looking for how to send an anonymous text from an iPhone or secure their banking data, zero-trust provides the foundation.
Let those early wins build momentum.
Whether you’re tightening app API security, ensuring runtime app security, or designing a truly secure mobile architecture, the journey is worth it.
Apps that adopt zero-trust best practices today will be the ones users trust tomorrow.
Build safer. Build smarter. Built with zero-trust at the core.
FAQs
- What is zero-trust mobile security?
Zero-trust mobile security is a framework where no device, user, or app is automatically trusted. It uses continuous verification, app hardening, and mobile IAM to protect data and users at every layer.
- Why is zero-trust important in mobile app development?
Mobile apps face constant threats: malware, API abuse, and data leaks. Zero-trust architecture helps protect by assuming every access request must be verified, reducing the attack surface significantly.
- Can I add zero-trust to an existing app?
Yes! You can integrate zero-trust SDKs, app API security, and runtime app security into existing apps. Start with basic authentication upgrades and work toward full secure mobile development.
- Does zero-trust slow down the app experience?
Not if done right. With tools like dynamic permission checks and risk-based access, you can stay secure without hurting performance or UX.
- How do I choose a development partner for zero-trust apps?
Look for experience in zero-trust mobile, secure mobile architecture, and mobile app endpoint security. Companies like Boolean Inc. specialize in building secure, scalable, and trusted mobile apps.
- What is digital secure app on Android?
Digital secure apps on Android are security solutions that protect your device using zero-trust principles, monitoring for threats and securing your data.
- Is t-mobile secure as good as digital secure?
Both implement zero-trust principles, but effectiveness varies based on specific features and implementation.
- Is Verizon Digital Secure safe?
When properly configured with zero-trust principles, carrier security apps provide robust protection.







