Introduction
Your phone holds your entire life. Banking apps. Private messages. Health data. Photos of your kids.
Right now, all of that is protected by encryption that’s worked perfectly for decades.
But here’s the thing: there’s a ticking time bomb headed our way. It’s called quantum computing.
Do not panic yet. We have got time to prepare. But we need to start now.
The Global Post Quantum Cryptography market size was estimated at USD 1.15 billion in 2024 and is expected to increase at a CAGR of 37.6% from 2025 to 2030.
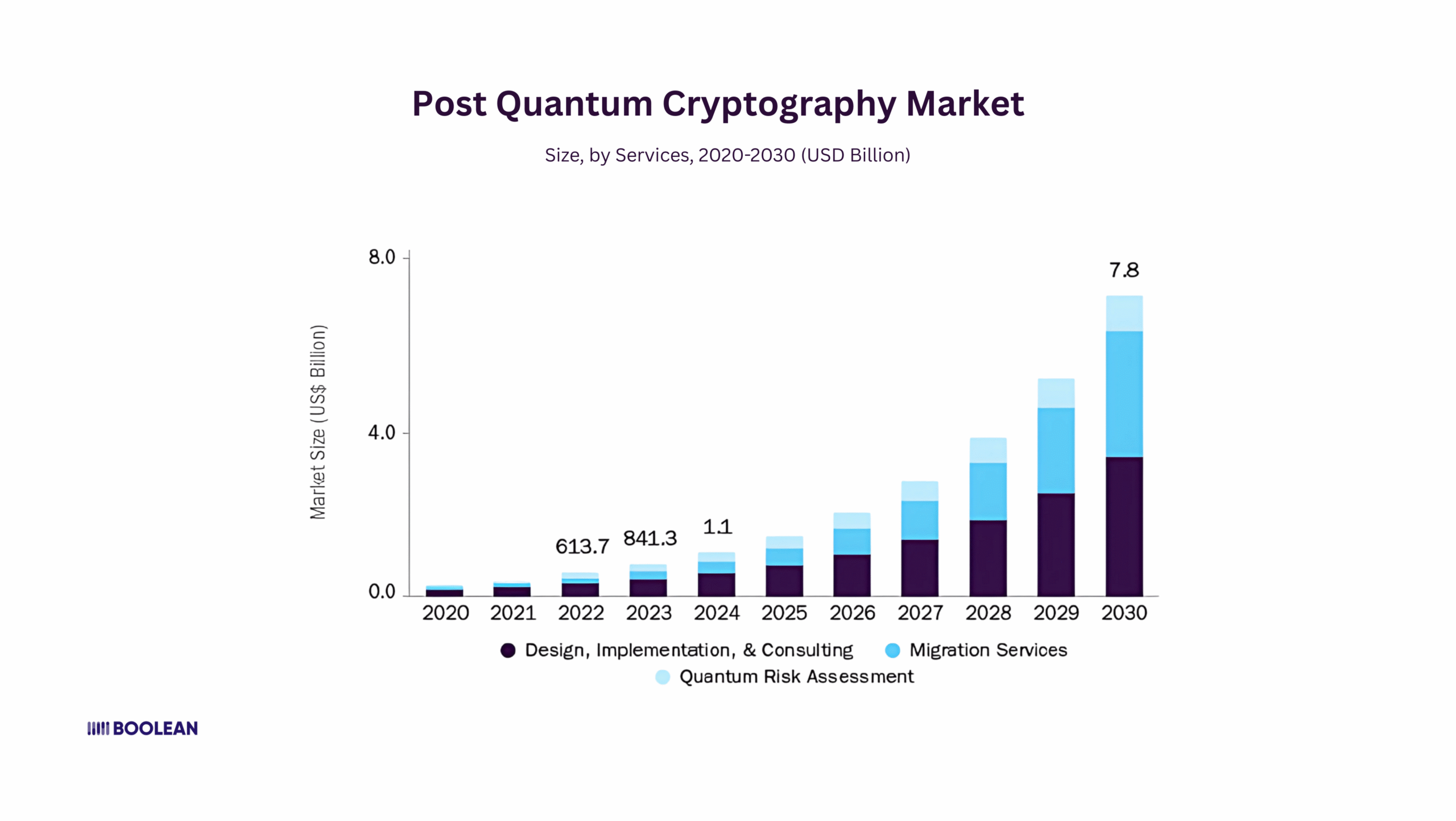
This is not just a random figure. This is a wake-up call. Major companies and governments are already putting billions into quantum-safe solutions because they know what is coming.
So, is there really post quantum cryptography? Think of it as the next generation of digital locks. Who cannot even break super-powerful quantum computers.
And if you’re building mobile apps, you need to understand this stuff. Not tomorrow. Not next year. Today.
Here’s why this matters to you personally.
Quantum computers aren’t science fiction anymore. Tech giants like Google, IBM, and others have working quantum machines. They’re getting more powerful every year. Once they reach a certain level, they’ll crack current encryption like it’s nothing.
Imagine someone having a master key to every digital lock in the world.
Scary? Absolutely.
But here’s the good news: we’re not sitting ducks. Post quantum cryptography is our defense. It’s a completely new approach to keeping data safe.
And the best part? You don’t need a PhD in quantum physics to implement it in your mobile apps.
We’ll cover what quantum computers can actually do, which new encryption methods work best for mobile apps, and how to start protecting your users today.
Because waiting until quantum computers become mainstream? That’s like waiting until your house is on fire to install smoke detectors.
Your users trust you with their data. Let’s make sure that trust isn’t misplaced when the quantum era arrives.
Ready to future-proof your mobile apps? Let’s dive in.
What is Post Quantum Cryptography (PQC)?
Let me explain this in the simplest way possible.
You know how your mobile app uses passwords and encryption to protect data? This is like a complex lock on your door.
Right now, these locks work great. Even the world’s fastest computers would need millions of years to pick them.
But quantum computers? They’re like having a skeleton key.
Post quantum cryptography is our answer to this problem. It’s a collection of new mathematical locks that even quantum computers can’t pick. Pretty cool, right?
Here’s the thing that confuses most people: post quantum cryptography isn’t about using quantum mechanics to protect data.
Nope. It’s actually the opposite. It’s about creating encryption methods that stay strong even when quantum computers attack them.
Think of it this way. Current encryption is like a maze with one correct path. Regular computers try every possible route, which takes forever. Quantum computers can explore all paths simultaneously. They find the exit almost instantly.
Post quantum cryptography builds a different kind of maze. One where even exploring all paths at once doesn’t help.
So what makes these new methods special?
They rely on math problems that are hard for both regular AND quantum computers. Problems like finding the shortest path through a multi-dimensional lattice.
Or decoding seemingly random data without the key.
The beauty is, your mobile app doesn’t need quantum technology to use post quantum cryptography. It runs on regular phones. Regular servers. Regular everything.
You’re just using smarter math to stay ahead of future threats.
Now, you might be thinking: “If it’s so great, why aren’t we using it already?”
Good question. There are a few reasons.
- First, we’ve been testing and perfecting these methods for years. You don’t want to rush security.
- Second, current encryption still works fine; quantum computers aren’t powerful enough to break it yet.
- And third, switching millions of apps and systems takes time.
But here’s what’s changed: the standards are finally ready.
The NIST (National Institute of Standards and Technology) has officially approved several post-quantum algorithms. It is like obtaining the official rule book for the new game, which everyone needs to play.
For mobile developers, this means you now have clear, tested options. You’re not experimenting anymore. You’re implementing proven solutions.
The core idea remains simple. Post-quantum cryptography protects your app’s data from both today’s threats and tomorrow’s quantum computers. It’s like insurance for the digital age.
And the best part? Your users won’t even notice the difference. Their apps will work the same. They’ll just be protected by mathematics that even quantum computers can’t crack.
Ready to see which specific algorithms you should consider for your mobile app? That’s exactly what we’ll explore next.
Understanding the Quantum Computing Threat
Let’s chase. Why should you care about a quantum computer?
Because they are going to make every password, every encrypted message, and every safe transaction in your mobile app.
Not today, not tomorrow. But soon it is so much that you need to work now.
What makes the quantum computer so dangerous here?
A regular computer processes information in ones and zeros (0s and 1s). They try each possibility at a time. It is like trying to find the right key by testing each one on your keyring. Slow but stable.
Quantum computers? They use qubits. These can be one, zero, or both at the same time.
Weird, right? It’s like trying all the keys on your keyring simultaneously. That’s the superpower that breaks our current security.
The math is terrifying. A problem that would take a regular computer billions of years? A quantum computer might solve it in hours.
Your RSA encryption? Broken. Your ECC certificates? Toast. That secure messaging feature you’re so proud of? Completely exposed.
But when will this actually happen?
Experts call it “Q-Day”, the day quantum computers become powerful enough to break current encryption. Most predict it’s 10-15 years away. Some say sooner. IBM, Google, and others are racing to get there first.
Here’s the kicker: Hackers are already preparing. They are now stealing encrypted data; they plan to decrypt it later when the quantum computer arrives.
Think about your mobile app. What data will still matter in 10 years? Medical records? Financial information? Personal messages? If it’s worth protecting now, it’s worth protecting from future quantum attacks.
We won’t get much warning. One day, quantum computers won’t be powerful enough. The next day, they will be. And every piece of data protected by old encryption becomes instantly vulnerable.
For mobile apps, the threat is especially serious. Phones store incredibly personal data. They’re always connected. And most users never update their apps. That outdated encryption? It’s a ticking time bomb.
The good news? We’re not helpless. Post quantum cryptography is our shield. But only if we implement it before Q-Day arrives.
Your users are counting on you to protect their data. Not just from today’s hackers, but from tomorrow’s quantum computers too.
How PQC Works (Without the Math Headache)
At its core, post-quantum cryptography works by using mathematical problems that even quantum computers can’t solve efficiently.
Instead of the prime number puzzles behind RSA or the elliptic curves used in ECC, PQC leans on tougher challenges, ones that don’t crumble under quantum algorithms.
One of the most promising families is lattice-based cryptography.
Other approaches include code-based, hash-based, and multivariate polynomial systems. Each has its strengths, but lattice-based methods are currently leading the race in the NIST PQC standards.
Here’s the trick for mobile developers: PQC doesn’t have to replace today’s encryption overnight. Many are starting with hybrid encryption, pairing PQC with classical algorithms.
In this way, even if one method fails, the other still stands.
It’s extra protection without making life harder for your users.
NIST PQC Standards and the 2025 Adoption Landscape

When it comes to Quantum Cryptography, a question always comes: what algorithms should we use? This is where NIST – U.S. National Institute of Standards and Technology – Steps.
Since 2016, the NIST has been running an international competition to find the best quantum-resistant algorithm.
By 2025, these algorithms will be the go-to standards for anyone serious about PQC adoption.
The main picks include:
- FIPS 203: ML-KEM (Kyber) — a KEM for key exchange. Fast, compact, and the leading choice for hybrid TLS handshakes on mobile.
- FIPS 204: ML-DSA (Dilithium) — a digital signature scheme. The go‑to for certificates, code signing, and identity with moderate signature sizes.
- FIPS 205: SLH-DSA (SPHINCS+) — hash‑based signatures. Very conservative and robust; larger signatures, best where long‑term trust matters most.
- Coming next: Falcon (a compact lattice‑based signature) and Classic McEliece (code‑based KEM) are in the standardization pipeline; watch for updates as they mature.
The 2025 adoption picture (what you can expect)
- TLS/QUIC: Hybrid key exchange (e.g., X25519 + Kyber) is moving into production across major TLS stacks and CDNs. It keeps current security while adding quantum‑safe cryptography, with manageable overhead for mobile apps.
- X.509 certificates and PKI: PQC and hybrid signatures are being piloted. Public WebPKI acceptance is gradual; internal PKI and mTLS deployments will adopt PQC sooner. Plan for bigger certs and chain sizes.
- End‑to‑end protocols: Messaging ecosystems are testing PQC (e.g., Signal’s PQXDH, Apple iMessage’s PQ enhancements). MLS and HPKE drafts add PQ KEMs; expect early interop in 2025.
- Compliance signals: NSA CNSA 2.0 sets migration expectations for U.S. National Security Systems starting now through the late 2020s, pushing vendors and regulated sectors toward PQC adoption.
- FIPS 140‑3 validation: Crypto modules that implement ML‑KEM/ML‑DSA will begin appearing on the validation lists. If you’re in a regulated industry, pick libraries with a clear FIPS roadmap.
Ecosystem and libraries snapshot
- OpenSSL 3.x (via providers like Open Quantum Safe), BoringSSL, wolfSSL, and mbed TLS have PQC/hybrid options, some behind flags or “experimental” labels.
- Java/Kotlin/Swift: Bouncy Castle and emerging bindings (plus Rust crates via FFI) bring PQC to mobile; Google Tink and platform SDKs are tracking PQC support.
- Platform key stores (Android Keystore, iOS Keychain/Secure Enclave) handle symmetric keys and wrapping as usual; PQ public‑key ops are typically done in app or via your TLS library for now.
For mobile developers, this is big news. Following NIST PQC 2025 standards means you’re not gambling on untested crypto. You’re building on algorithms that have been stress-tested by the global cryptography community.
And adoption is already taking momentum. Messaging apps, VPNs, and Cloud Services are experimenting with hybrid cryptography, a combination of PQC with classical methods to ensure a smooth transition.
This approach not only promotes crypto-agency but also helps with concerns of real-world performance on mobile devices.
If your mobile app handles sensitive data, now is the time to align with NIST PQC standards.
Waiting until quantum computers arrive is like buying a fire extinguisher after the house has already caught fire.
Key Post-Quantum Algorithms for Mobile Apps
Let’s talk about which algorithms actually work for mobile apps. Because not all post-quantum solutions are created equal.
Your phone has a limited battery. Limited processing power. Limited bandwidth. So we need algorithms that are both quantum-safe AND mobile-friendly. Lucky for us, we’ve got some solid options.
ML-KEM (Module-Lattice-Based Key Encapsulation)
This is your go-to for encrypting data. It’s based on lattice cryptography. Imagine a multi-dimensional grid where finding specific points is super hard. Even for quantum computers.
Why mobile developers love it:
- Fast. Really fast. Sometimes faster than current encryption
- Small key sizes (compared to other PQC options)
- Battery-friendly
The downside? Slightly larger data packets. But we’re talking kilobytes, not megabytes.
ML-DSA (Module-Lattice-Based Digital Signatures)
Need to verify that data hasn’t been tampered with? This is your algorithm. It creates digital signatures that prove authenticity. Think of it as a quantum-proof seal of approval.
Perfect for:
- App updates verification
- Transaction signing
- API authentication
The trade-off: signatures are bigger than current methods. But for most mobile apps? Totally manageable.
SLH-DSA (Stateless Hash-Based Signatures)
This is your backup option. It’s based on hash functions, the same tech that powers blockchain. Super secure. Super reliable. But also super slow.
When to use it:
- Critical operations that rarely happen
- When you need maximum security
- As a fallback option
Honestly? Most mobile apps won’t need this one. But it’s nice to have options.
Hybrid Approaches: The Smart Choice
Here’s the secret sauce. You don’t have to pick just one. Smart teams are using hybrid encryption, combining classical algorithms with post-quantum ones.
For mobile apps, hybrid usually means:
- RSA or ECC + ML-KEM for encryption
- ECDSA + ML-DSA for signatures
Choosing the Right Algorithm
So which should you use? Here’s my simple guide:
- Messaging app? Go with ML-KEM. It’s fast enough for real-time chat.
- Banking app? ML-DSA for transaction signing. Security over speed.
- E-Commerce? Hybrid approach. Balance performance with protection.
- Gaming? Stick with ML-KEM for now. Keep those frame rates high.
The best part? You don’t need to understand the math. Modern libraries handle the complexity. You just need to know which tool fits your job.
Remember: these aren’t experimental anymore. They’re NIST-approved. Battle-tested. Ready for production. The same algorithms protecting government secrets can protect your users’ selfies.
One final tip: start with key encapsulation (ML-KEM). It’s the easiest to implement and gives immediate protection. Add signatures later. Walk before you run.
Your mobile app doesn’t need every algorithm. It needs the right algorithm. Choose based on your needs, not on what sounds most impressive.
Ready to actually implement these in your app? Let’s dive into the practical stuff.
Implementing PQC in Mobile Applications
Alright, let’s get practical. You understand the threat. You know the algorithms. Now comes the fun part, actually building this into your app.
First things first: you don’t need to rewrite everything. It’s more like upgrading your car’s engine while keeping the same body.
- Start with Hybrid Encryption
Here’s the golden rule: never go full PQC on day one. Use hybrid encryption instead. It’s like wearing suspenders AND a belt. Overkill? Maybe. But your users’ data stays protected no matter what.
Current encryption + Post-quantum encryption = Happy users
This approach solves multiple problems. Compatibility with older devices? Check. Protection against current threats? Check. Future-proofing against quantum attacks? Double-check.
- Performance Considerations
PQC algorithms are bigger. Yes, they can be slower. But here’s what actually matters for mobile:
ML-KEM encryption? Only 5-10% slower than current methods. Most users won’t even notice. Especially if you implement it smartly.
The real challenge? Key sizes. A typical ML-KEM public key is about 1KB. Current RSA keys? 256 bytes. That’s 4x bigger. For a messaging app sending thousands of keys, that adds up.
But here’s the thing: we’ve solved bigger problems before. Remember when apps jumped from 3G to 4G? Same idea. Optimize what you can. Accept what you can’t.
- Battery Optimization
Your users care about battery life. A lot. So here’s how to implement PQC without draining their phones:
Cache everything. Seriously. Don’t regenerate keys for every operation. Store them securely and reuse when possible.
Batch operations. Instead of encrypting each message separately, group them. One PQC operation for multiple items. Your battery will thank you.
Use hardware acceleration when available. Modern phones have crypto chips. They’re not PQC-optimized yet, but they help with the hybrid approach.
- Bandwidth Optimization
Larger keys mean more data. More data means slower apps. Here’s how to minimize the impact:
Compress before encrypting. Sounds obvious, but you’d be surprised how many developers forget this. Smaller payload = faster transmission.
Use session keys. Exchange PQC keys once, then use smaller symmetric keys for actual data. It’s like exchanging house keys instead of rebuilding the lock each time.
Implement progressive encryption. Critical data gets full PQC protection. Less sensitive stuff? Maybe just hybrid. Be smart about your security levels.
- Testing Your Implementation
Test on old phones. That 3-year-old Android device? If PQC works there, it’ll work anywhere.
Monitor your metrics:
- Encryption time
- Battery usage
- Network traffic
- App size
Set acceptable thresholds. Maybe 20% slower is OK. Maybe 50% isn’t. Know your limits before your users find them.
Real-World Implementation Strategy
Here’s your roadmap:
- Week 1-2: Add PQC libraries to your project. LibOQS for cross-platform. Bouncy Castle for Java. Pick what works for your stack.
- Week 3-4: Implement hybrid key exchange. Start with your login flow. It’s contained, testable, and critical.
- Week 5-6: Extend to data encryption. Messages, files, whatever your app protects. Go slow. Test everything.
- Week 7-8: Performance optimization. Profile your app. Find the bottlenecks. Fix what matters, ignore what doesn’t.
Code Architecture Tips
Make your crypto layer abstract. Seriously. Don’t hardcode algorithm choices. Use interfaces like:
text
CryptoProvider.encrypt(data, algorithm)
This way, switching algorithms later is trivial. Crypto-agility isn’t just a buzzword; it’s survival.
Keep your classical and PQC paths separate but parallel. If PQC fails (bugs happen), you can fall back to classical. Your users stay protected either way.
Common Pitfalls to Avoid
Don’t encrypt everything. Seriously. Public data doesn’t need quantum protection. Be selective.
Don’t forget about backwards compatibility. Users with older app versions still need to communicate with the updated ones.
Don’t implement your own crypto. Ever. Use established libraries. This isn’t the place to be creative.
The bottom line? Implementing PQC in mobile apps is totally doable. It requires planning. It requires testing. But it doesn’t require miracles.
Start small. Test thoroughly. Scale gradually. Your future users will thank you for thinking ahead.
Crypto-Agility: Building Flexible Security
If there is a truth about safety, it is: what is strong today can be weak tomorrow. This is the reason that crypto-agency is no longer optional. This is necessary.
Crypto-agency means designing your mobile app so that you can quickly swap the encryption algorithm, without separating the entire system.
After quantum cryptography, this flexibility is necessary. We are still in the PQC era, and standards may develop. A new algorithm may prove to be rapid, safe, or more mobile-friendly.
With Crypto-Agility, you can pill the major downtime or without expensive rewrites.
Practical tips for mobile apps:
- Abstract your crypto layer: Keep encryption code separate from core app logic.
- Support multiple algorithms at once: Makes migration smoother and enables hybrid encryption.
- Follow NIST PQC updates: Stay aligned with evolving standards.
- Test migrations early: Practice swapping algorithms in staging environments before it’s urgent.
The goal isn’t just to survive the quantum threat mobile world. It’s to adapt as that world changes, without panicking or breaking your app in the process.
End-to-End Post-Quantum Security for Mobile
Your users expect their messages to be private. Their photos are personal. Their data remains theirs.
End-to-end encryption promises all of that. But what happens when quantum computers arrive?
Time to quantum-proof the entire chain.
The Complete Security Picture
End-to-end security isn’t just about encrypting messages. It’s about protecting every single touchpoint. From the moment users type to the moment recipients read. Every step needs quantum protection.
Here’s what most developers miss: securing data in transit isn’t enough. You need to think about:
- Data at rest on devices
- Backup encryption
- Key exchange protocols
- Authentication tokens
- Even metadata
One weak link? Your entire chain breaks.
PQC for Messaging Apps
Let’s start with the obvious use case. Messaging apps live or die by their encryption. WhatsApp, Signal, iMessage, they all promise privacy. But current protocols won’t survive quantum attacks.
The fix? Upgrade your key exchange first. That’s where quantum computers do the most damage.
Use ML-KEM for exchanging session keys. Keep using AES for actual message encryption (it’s already quantum-resistant for symmetric encryption).
Here’s the beautiful part: users won’t notice. Messages are sent just as fast. The app looks identical. But underneath? Quantum-proof armor.
Securing Data at Rest
Your phone is a treasure trove of data. Photos. Documents. Cached messages. Most apps encrypt this stuff. But with what?
Time for an upgrade. Use hybrid encryption for stored data. PQC for the key wrapping, traditional AES for bulk encryption. It’s the best of both worlds, quantum safety without killing performance.
Pro tip: Don’t forget about backups. Cloud backups, especially. That data might sit there for years. Decades even. Perfect target for “harvest now, decrypt later” attacks.
Authentication
Passwords are already weak. Quantum computers will make them irrelevant. But here’s the thing: PQC isn’t just about encryption. It’s about authentication, too.
Digital signatures prove identity. ML-DSA makes those signatures quantum-safe. Use them for:
- Login tokens
- API authentication
- Transaction verification
- Code signing
Every time your app says “yes, this is really the user,” make sure quantum computers can’t forge that answer.
Protecting the Metadata
Everyone focuses on message content. But metadata tells stories too. Who talked to whom? When. How often. For how long?
Quantum computers make traffic analysis easier. They can break the patterns hiding your metadata. The solution? Onion routing with PQC.
Multiple layers of quantum-safe encryption. Each hop only knows the next destination.
It’s not paranoid if quantum computers really are that powerful.
Real-World Implementation Example
Here’s how a messaging app might implement full PQC protection:
- User opens app → Authenticate with ML-DSA signatures
- Start new chat → Exchange keys using ML-KEM
- Send message → Encrypt with AES using quantum-safe keys
- Store locally → Hybrid encryption for data at rest
- Backup to cloud → Additional PQC layer for long-term storage
Each step is protected. Each link is quantum-proof.
Performance
Full end-to-end PQC adds overhead. Maybe 10-15% in total. But here’s the thing: users won’t notice if you’re smart about it.
Key exchanges happen once per conversation, not per message. Signatures verify on login, not every action. Bulk encryption stays fast with symmetric algorithms.
The overhead is front-loaded. Once the secure channel exists, it’s business as usual.
Testing Your E2E Implementation
You can’t just assume it works. Test scenarios like:
- What if one user has PQC and another doesn’t?
- Can quantum-safe messages sync across devices?
- Do encrypted backups restore properly?
- Does the app gracefully handle algorithm transitions?
Edge cases matter more with E2E encryption. One broken link compromises everything.
Real-World Examples and Case Studies
Post quantum cryptography isn’t just a research topic anymore; it’s quietly making its way into everyday mobile experiences. Here’s how it’s showing up in the real world.
Healthcare data is a prime target for attackers.
Some healthcare apps are now testing end-to-end PQC to protect patient reports and imaging results, ensuring that sensitive health records stay private even against future quantum attacks.
In a zero-trust mobile security setup, no one, not even the backend, can access unencrypted patient data.
Ephemeral messaging sounds safe, but without PQC, stored backups or intercepted messages could be decrypted years later.
Some social apps are piloting hybrid cryptography, so even temporary content has long-term protection.
- Fitness App Security
Popular fitness apps often track location and health metrics.
Developers are beginning to combine PQC with composable architecture, so the encryption module can be swapped or upgraded without touching other parts of the app.
This approach keeps both user trust and the speed of development.
Think a language learning app doesn’t need quantum security? Many collect payment details, track progress, and store personal data.
Using PQC within a serverless architecture and Backend-as-Service (BaaS) setup ensures that the data is safe in the distributed system without slowing the user experience.
For enterprise tools, PQC adoption is moving even faster. B2B mobile apps often handle contracts, financial data, and business secrets.
A PQC-competent crypto-egency framework allows them to meet strict compliance requirements while preparing for future algorithm changes.
Across these examples, one theme stands out: PQC works best when paired with adaptable design choices, like composable architecture, serverless systems, and zero-trust models.
This keeps apps ready not just for today’s threats, but for whatever quantum computing brings next.
Partner with Boolean Inc. for Quantum-Safe Mobile Security
Moving to post-quantum cryptography can feel overwhelming, but you don’t have to do it alone.
Boolean Inc. specializes in helping mobile users adopt NIST PQC standards, implement hybrid encryption, and build crypto-agility into their apps from day one.
Whether you’re securing a medical diagnosis app, a B2B mobile platform, or the next big social network, our team can guide you through strategy, integration, and performance tuning, without slowing down your release cycles.
Quantum threats are coming. Let’s get your app ready before they arrive.
Conclusion
Quantum computing is set to reshape digital security, and the change won’t be gradual.
Once these systems reach a practical scale, the encryption most mobile apps rely on today could be broken in hours.
That’s why preparing with post-quantum cryptography isn’t a luxury; it’s a necessity.
The best approach is to start early. Experiment with new encryption methods, test hybrid setups, and design your systems so security can evolve without breaking your app.
This preparation ensures you’re ready for future threats without scrambling under pressure.
The quantum era is coming faster than most expect. The decisions you make now will determine whether your mobile app stays secure or becomes vulnerable the moment the technology tips.
FAQs
- Will post quantum cryptography make my app slower?
Only by 5-10%. Most users won’t notice. The bigger change is app size, expect 10-20MB extra for PQC libraries. Modern phones handle it fine.
- Do I need to implement PQC right now, or can I wait?
Start now with hybrid encryption. Migration takes years, and hackers are already collecting data to decrypt later. Better prepared than panicked.
- Which post quantum algorithm should I choose for my mobile app?
ML-KEM for encryption, ML-DSA for signatures. They’re NIST-approved and mobile-friendly. Use hybrid approaches for best results.
- How much will PQC implementation cost my development team?
Mainly development time, about 4-8 weeks. The algorithms are free and open-source. Think of it as insurance, not an expense.
- Can older phones handle post quantum cryptography?
Phones from the last 3-4 years work fine. For older devices, use crypto-agility to adjust protection levels. Everyone stays secure.







